While the promise of RASP is attractive, many customers have been disappointed to find that current RASP systems only cover a fraction of their application stack and often require modifications to source code—impractical for most enterprises. There is also a growing consensus that current RASP tools are more appropriate for use by application developers (DevOps) and less so for security professionals (SecOps) who need broad coverage, reliability and accuracy, without the extensive tuning or code modification that comes with the current generation of RASP products.
Virsec has extended the concept of self-protection to cover the full surface of application code, while delivering broader, deeper and more precise security than any existing RASP product. Virsec also delivers security that is effective and practical for SecOps teams, precisely securing any application without code changes or tuning.
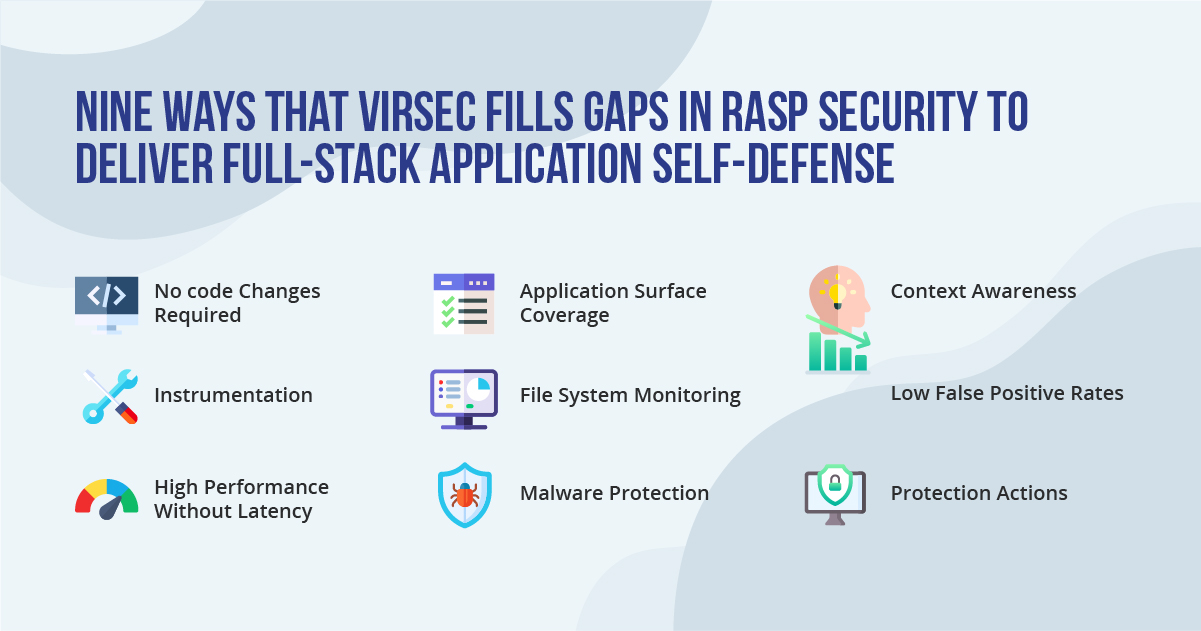
Read more about the 9 ways That Virsec Fills Gaps in RASP Security to Deliver Full-Stack Application Self-Defense
Virsec is designed to be easy to deploy and fit seamlessly into SecOps environments. Virsec installs in minutes, requires no modifications to code, custom configuration or tuning, delivering immediate attack protection. Virsec architecture scales easily with on-premises,
cloud or container deployments, with lightweight App Sensors deployed on application servers, and a high-performance Analysis Engine detecting attacks and taking protection actions within milliseconds.
Virsec performs all analysis locally within the application environment. With Virsec high-performance architecture, lightweight App Sensors monitor application activity at multiple locations in code, while a local Analysis Engine makes near real-time determination about attacks and takes protection actions within milliseconds.
Virsec extends the promise of self-defending applications to the entire web application stack, including web apps, servers, back-end applications, file systems, process memory and binary code. This is critical to SecOps teams that must protect a wide range of in-house and third-party applications, without access to source code.
Virsec takes a holistic approach to application security protecting code, inputs, databases, processes, memory and file systems. Few attacks are monolithic, but most attacks manipulate legitimate files to corrupt processes, ransom data or inject malicious code. Virsec monitors all files associated with critical applications and can instantly spot illicit changes that indicate attacks. Automated protection actions include quarantining suspicious files, restoring changed files, and alerting external backup tools to restore critical data.
Virsec delivers comprehensive protection against the widest range of vulnerabilities, conventional malware, fileless attacks, memory exploits, and attacks that weaponize at runtime. Virsec can successfully defeat zero-day attacks and advanced cyber kill chains the first time, without prior, heuristics or predictive training.
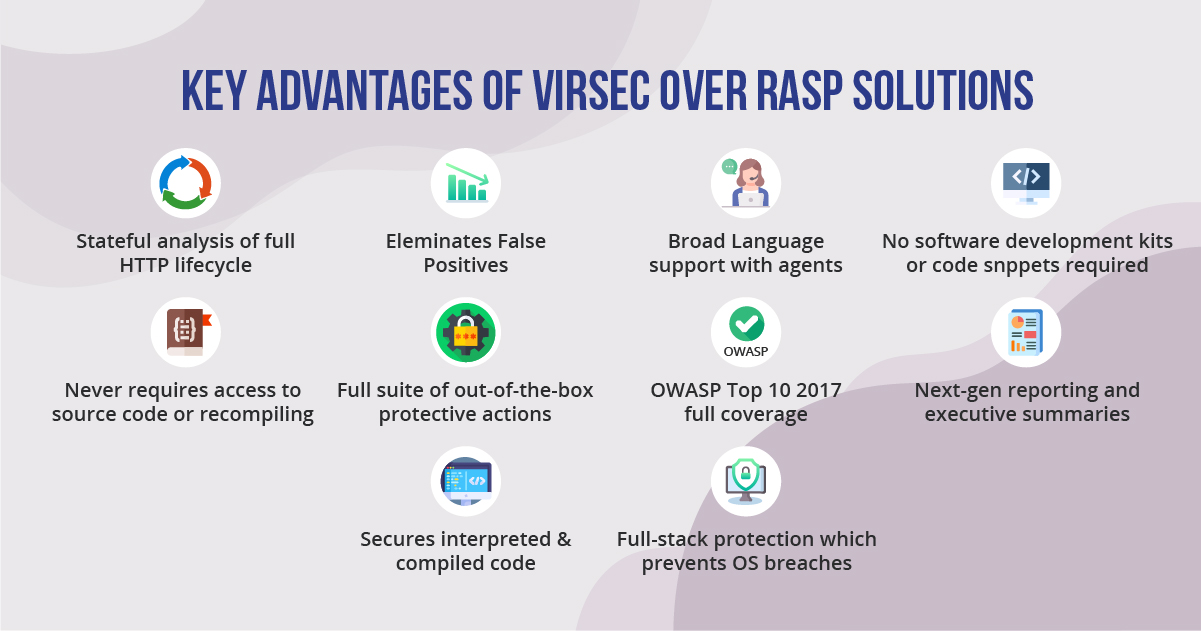
Virsec is unique in understanding the complete context of applications, providing integrated stateful inspection of the full request and response lifecycle as well as commands affecting the OS and file system. With this process, Virsec definitively separates possible threats from actual attacks, eliminating false positives. Virsec detects and stops these attacks in real-time during application runtime.
Virsec has pioneered deterministic security that eliminates the time and expense of false positives. Through deep, stateful analysis of the entire request/response process, as well as unique abilities to map and guardrail acceptable application behavior, Virsec separates the noise of possible threats from the immediate dangers of real attacks, allowing SecOps teams to precisely pinpoint and stop the most advanced cyber kill chains.
Virsec delivers a broad range of automated protection actions that stop attacks in their tracks without user intervention. These include terminating rogue user web sessions or IP connections, blocking command injections, quarantining and restoring corrupted files, and stopping rogue processes. In addition, Virsec integrates with existing security products such as firewalls and WAFs to enforce access controls through existing channels.
To know more about TeBS’ Cybersecurity expertise, click here.